The Compliance of a New Idea
| ✓ Paper Type: Free Assignment | ✓ Study Level: University / Undergraduate |
| ✓ Wordcount: 2974 words | ✓ Published: 12 Aug 2019 |
Contents
Article 30 Record of Processing
Data Protection Impact Assessment
Introduction
For the purpose of this assignment I have chosen to evaluate the compliance of a new idea, that I would like to introduce in the course of my day to day task performance at work, to enhance efficiency and gain greater control over the monitoring of transactions performed within my role at a financial services organisation with the General Data Protection Regulation 2016/679.
I need to perform this monitoring as a legal requirement under the Criminal Justice Act 2018. Which requires the financial services sector to gain an even greater understanding of the transaction norms for various account types and take a risk-based approach to monitoring and compliance with the Criminal Justice Acts.
In my new role as MLRO, the principles of the GDPR will be of great assistance to compliance with the new Criminal Justice (Money Laundering and Terrorist Financing) (Amendment) Act 2018 and the 4th EU AML Directive (and soon to be 5th AML Directive).
The CJA 2018, Part 2 Section 4, K(b) requires that data controllers and processors “documents, data and information on customers are kept up to date in accordance with its internal policies, controls and procedures”(Ireland, 2018); which is also required in accordance with the General Data Protection Regulation (EU) 2016/679, namely that the data is kept “accurate, complete and up to date” (principle 4) (European Parliment, 2016).
Both Acts (Data Protection Act 2018 and CJ Act 2018) require data controllers to maintain up to date records and under this requirement the retention of records is highlighted. Data should be retained no longer than is necessary for the purpose or purposes it was initially provided. A Data Retention Policy should clearly set out the flow of data through an organisation form the initial customer/member onboarding stage all the way through to data deletion and destruction when the data no longer meets with the retention schedule deadline.
During the flow of data through the organisation, the data controller is expected to ensure that it has adequate technical and organisational security measures in place to prevent unauthorised or unlawful processing and accidental loss, destruction or damage to personal data (Principle 3).
Article 30 Record of Processing
| Data Controller
Financial Services Provider Ltd. 01 12345678 |
Record of Processing Activities | Data Protection Officer
Joan Smith 01 12345678 |
||||||
| Data Category | Data Subject Category | Lawful basis of Processing | Record Retention Limit | Transfers to Third Countries | Security Measures in Place | Categories of Recipients
|
||
| Account transactions | Personal Data – (Sensitive Data to most individuals) | Performance of a contract.
Compliance with legal obligation for ML/CFT monitoring. |
Lifetime of the relationship +7 years | N/A | Password Security on all PC’s being accessed, with access rights authorised by appropriate Senior Management. | Garda Investigation Bureau/Financial Investigation Unit -FIU and Revenue Commissioners.
Internal/External Auditors. |
||
| AML Categorisation- Risk Levels
(Not subject to Subject Access Request) |
Personal Data | Legal Obligation | Lifetime of relationship +5 years | N/A | Password Security on all PC’s being accessed, with access rights authorised by appropriate Senior Management. | Garda Investigation Bureau/Financial Investigation Unit -FIU and Revenue Commissioners | ||
| AML Notes on system (Not subject to Subject Access Request) | Personal Data | Legal Obligation | Lifetime of relationship +5 years | N/A | Password Security on all PC’s being accessed, with access rights authorised by appropriate Senior Management. | Garda Investigation Bureau/Financial Investigation Unit -FIU and Revenue Commissioners | ||
Under Article 30 of the GDPR Data controllers no longer need to register the processing activities it undertakes with the Data Protection Commissioner. Instead Data Controllers need to comply with the six principles of the General Data Protection Regulation and clearly demonstrate accountability by ensuring it;
- Obtains and processes the information fairly, lawfully and in a transparent manner.
- Keep the information only for a specified purpose and process in a way that is compatible with the original purpose it was given.
- Keep the information safe and secure.
- Keep the information accurate, complete and up to date.
- Ensure the information is adequate, relevant and not excessive.
- Retain it no longer than is necessary for the specified purpose or purposes.[1]
By creating a record of processing data controllers have a useful tool in demonstrating their accountability and transparency to the office of the Data Protection Commissioners.
It is also a valuable tool in forming a data map or data inventory.
In creating a data map an organisation can see what data is held by each department.
This is especially important in meeting the new reporting obligation of 72 hours in the event of a data breach. The timeframe has also been reduced to one month (30 days) for requests of access to data received from an individual, where the identity has been verified.
All personal data relating to a living individual within the scope of the access requests, needs to be released. Information stored in emails also falls within the scope and will need to be retrieved. Voice recordings need to be transcribed and CCTV footage needs to be retrieved where possible. Any personal information of another individual must be redacted so as not to inadvertently cause a breach of another’s data in responding to the initial request. The more detailed the data inventory the easier it will be to pull all the required information together within the allotted timeframe. Where each department has played a part in creating a comprehensive data inventory the easier and quicker it will be for each department to respond to the lead on the response to the access request.
The fee of €6.35 has been removed and is only allowable in cases where the data controller can demonstrate that it would be onerous on the organisation or that there have been excessive requests made by the same individual. The onus is on the organisation to show this to be the case. Having a record of processing activities would be useful to the few organisations that this would be relevant to.
The new idea that I intend to implement falls outside the scope of an access request made by an individual. However, An Garda Siochana (usually not below the rank of Chief Superintendent- for a data request order. Data request orders can be made by a District Court Judge following on from a suspicious transaction report being submitted to An Garda Siochana in relation to data requests (Office of the Attorney General, 2010)) are permitted to access the information I will be processing where they send an official request for the release of data in the course of an investigation and the prevention of fraud. The Revenue Commissioners office will also receive details of any suspicious transactions or suspected occurrence of tax evasion as required by the relevant laws ( Office of the Attorney General, 1997).
Data Protection Impact Assessment
The General Data Protection Regulation was introduced in 2016, giving citizens greater control over how their personal information is processed, and those that have reason to be in possession of that data greater responsibility as to how they process the data. I appreciate the added responsibilities on data controllers and processors brought about by these changes in Data Protection legislation, I have always felt that business owners had an attitude of ownership over data once it enters their control, which I have never agreed with. Given my personal views on the responsibility to protect the personal information of others, I intend to do all I can to ensure my “new idea” meets with the GDPR’s rule of Privacy by Design (European Parliament, Council of the European Union , 2016).
As I process this idea, the main question I ask myself is; if I perform a Data Protection Impact Assessment on this idea would I be able to appropriately mitigate any risks of a data breach occurring?
My idea involves utilising Excel to extract the transaction data from our database. The IT system supports the exporting of these files to Excel format to gain further insight by running comparisons month by month, quarter by quarter and annually, in line with reporting requirements. The Excel file would then need to be edited using sorts and filters and pivot tables. This processing requires careful execution of edits to ensure that no cells are misrepresented as this could lead to incorrect initial conclusions being reached and if the error was not spotted immediately it could lead to false transaction levels being assumed, if no further scrutiny was to take place. Data protection principle of “accuracy” would apply here where the regulation clearly states that “personal data shall be: accurate and, where necessary, kept to date; every reasonable step must be taken to ensure that personal data are accurate, having regard to the purposes for which they are processed, are erased or rectified without delay” (European Parliament, Council of the European Union , 2016).
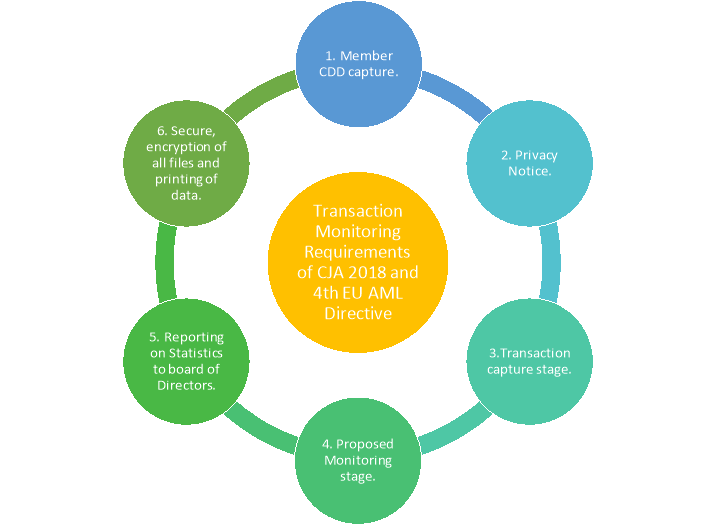
- Before any of the above actions take place, all user access rights are assigned to staff members by an appropriate senior management official. Whether the member wishes to open a new account, make a credit application, or making a request for online access (making a request for the use non-face-to-face transaction facility). Each staff member is assigned various user rights within their specific role. Any alteration of members data is logged and is fully auditable, within the IT system. Due to the nature of my role the information I intend to process using Excel has to be inaccessible to any other user within the organisation. These restrictions can be added within the IT system to ensure confidentiality.
- As per data protection regulation requirements for “Transparency”, members are provided with up to date privacy notices as they relate to each service they require. i.e. at account opening stage they are provided with an Account Opening Privacy Notice which has been written in an easy to understand format using plain English and providing the contact details of both the data controller and the DPO for further clarification on any of the points raised or to;
- make a subject ‘access’ request, (Article 15)
- request that their information is ‘rectified’, (Article 16)
- make a request to have their personal information ‘erased’ (known as the right to be forgotten) (Article 17)
- request to have a copy of their personal information (information supplied by the data subject) or request the information to be transferred to another data controller (‘data portability’) (Article 20)
- ‘object’ to automated decision making and profiling (this is the area that is of most relevance to my particular “new idea”, I will be basing my profiling activity on the legal obligation to monitor possible instances of fraud and tax evasion, both need to be reported on to FIU – Financial Investigation Unit and the Revenue Commissioners (Article 21 and 22)
- request a ‘restriction’ of processing where the data subject has question about the accuracy/lawfulness of processing of the data held by the data controller concerning him/her. (Article 18) (European Parliament, Council of the European Union , 2016)
- Transaction stage is performed only by authorised staff members under specific log in details relating to the function they are performing in capturing the correct transaction details as well as taking the opportunity to ensure that (KYC) customer due diligence information is both accurate and up to date. Both of these will ultimately feed into my excel data, by ensuring that our database is displaying the most up to date information available for CDD purposes I can be confident that as far as the information I pull from the database is 100% up to date, it is then up to me to ensure that all sorting/filtering and pivot tables are carried out carefully and no errors occur on this data.
- At the stage of pulling the data from the IT system to display in excel, all data fields need to be formatted correctly i.e. date/time etc. When the required data has been extracted successfully, this will be cross checked against the individual account, the relevant transactions and the categorisation level for the account type. ‘Profiling’ will be carried out. However, I will not utilise ‘automated decision making’ to decide if further monitoring of a specific account is warranted. This decision will be reached when compared to the live data on the IT system. At this point I need to ensure that my Excel data is secured and only the MLRO function is authorised to access this data to avoid any incident of unauthorised access to personal information as required by the General Data Protection Regulation; access to data should be based on a need to know basis only. This can be accomplished by the use of a separate folder on the system that is only accessed by the MLRO to store these reports. Access to the IT system spooler where the reports are run from should be blocked from displaying MLRO reports also.
- At the stage of reporting on findings to the board of Directors there will be no release of personal data, as the reporting is to be based on statistics, the MLRO report is not to refer to individuals or accounts. So, at this stage there will be no risk of a data breach occurring, once the data reported on is no longer linked to the original data source file.
- At the creation stage of the Excel spreadsheet that I plan to use, I will password protect each workbook that relates to the monitoring that is being performed on the data. I will password protect any resulting workbook or worksheets that can be linked back to the original data. All of this will be done within a secure profile set up on the network server. This data will be backed up as part of the normal end of day back up procedure run by the IT department.
During this process I have assessed if the need to create a more scalable reporting system would allow for the continued safeguarding of the personal information of the data subject.
I have determined that the risks are at the point of creating the Excel spreadsheet itself, as all appropriate information security measures are in place within the organisation. I can also assure that the file is created in a secure folder within the network, which is password protected and I am the only person (along with the CEO) that has access to this folder.
I would determine, that while I have a good working understanding of Excel and I would be relying on the prior knowledge of our compliance consultant on the use of the spreadsheet. One of the mitigates I would adopt would be an advanced training programme to be undertaken in the use of Excel, to eliminate the likelihood of human error.
With that training in place my findings would suggest that the usefulness of the Excel programme to monitor transacting norms would not infringe on the rights of the data subjects. When taken into consideration that this monitoring is a legal requirement and will be performed on the data for compliance purposes, it would be more beneficial to use the programme and ensure that this data is protected in the same manner as all other personal information held by the organisation in line with the data protection obligations. Namely, that the data is protected at all times from unlawful processing and accidental loss.
This information is not shared with other departments nor is it taken off site, so there is no risk posed of data being sent outside of the organisation with transfer to a third-party processor, where data processing agreements would need to be in place.
I would put forward the case, to allow processing on the data for this purpose to the Data Protection Officer for sign off. The remaining risk can be minimised by the above suggestion of advanced training and therefore the outcome that is achievable is proportionate to the potential risk involved.
Bibliography
Office of the Attorney General, 1997. Irish Statute Book. [Online]
Available at: http://www.irishstatutebook.ie/eli/1997/act/39/section/1002/enacted/en/html
[Accessed 18 12 2018].
European Parliament, Council of the European Union , 2016. CELEX_32016R0679_EN_TXT. [Online]
Available at: https://eur-lex.europa.eu/legal-content/EN/TXT/?qid=1528874672298&uri=CELEX%3A32016R0679
[Accessed 17 Dcember 2018].
European Parliment, C. o. t. E. U., 2016. EUR-Lex. [Online]
Available at: https://eur-lex.europa.eu/legal-content/EN/TXT/?qid=1528874672298&uri=CELEX%3A32016R0679
[Accessed 17 December 2018].
Ireland, G. o., 2018. Irish Statute Book. [Online]
Available at: http://www.irishstatutebook.ie/eli/2018/act/26/section/4/enacted/en/html#sec4
[Accessed 17 December 2018].
Office of the Attorney General, 2010. Irish Statute Book. [Online]
Available at: http://www.irishstatutebook.ie/eli/2010/act/6/section/63/enacted/en/html#sec63
[Accessed 18 12 2018].
(European Parliament, Council of the European Union , 2016, p. 35)
Cite This Work
To export a reference to this article please select a referencing stye below:
Related Services
View allDMCA / Removal Request
If you are the original writer of this assignment and no longer wish to have your work published on UKEssays.com then please click the following link to email our support team:
Request essay removal



